Technical Blog
 November 28, 2022
November 28, 2022
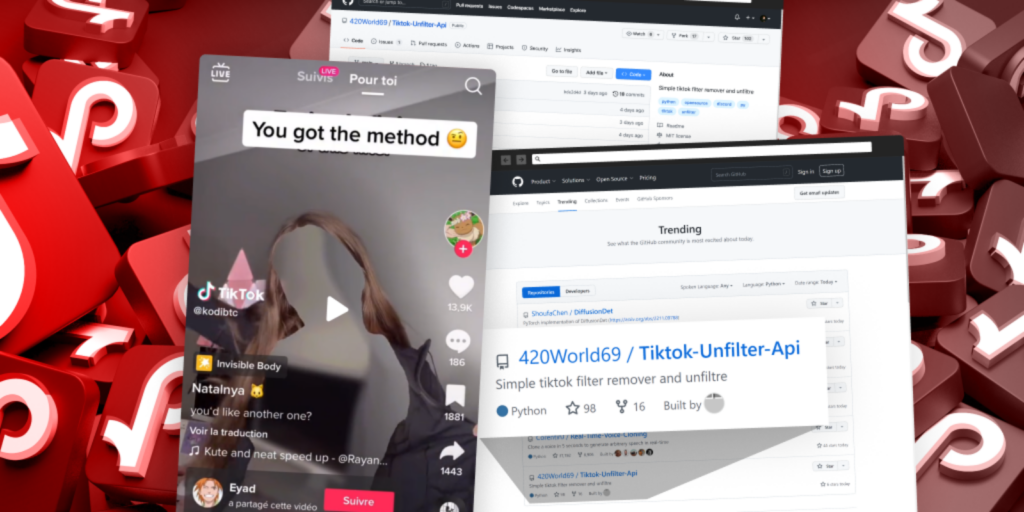
Attacker Uses a Popular TikTok Challenge to Lure Users Into Installing Malicious Package
 October 7, 2022
October 7, 2022
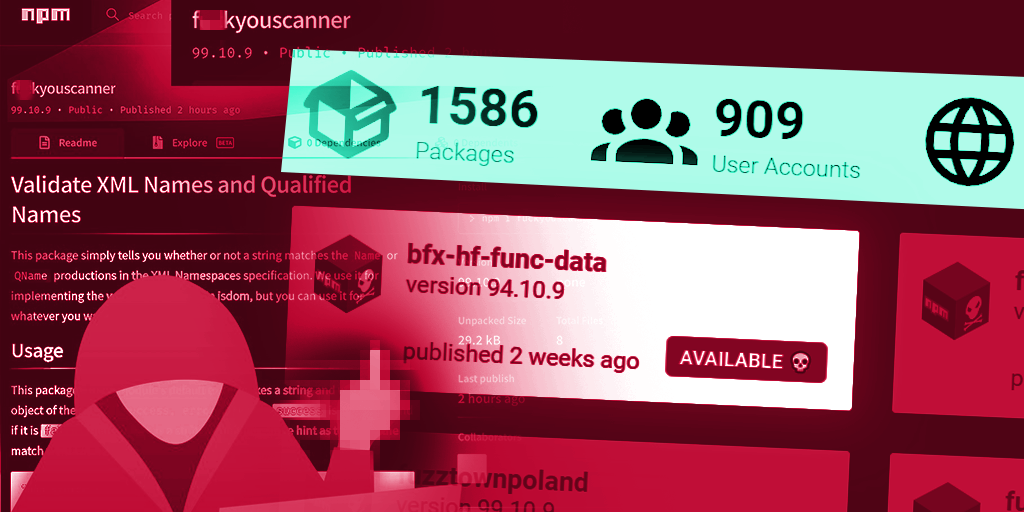
LofyGang – Software Supply Chain Attackers; Organized, Persistent, and Operating for Over a Year
 August 18, 2022
August 18, 2022
Amazon Quickly Fixed a Vulnerability in Ring Android App That Could Expose Users’ Camera Recordings
 August 17, 2022
August 17, 2022
Malicious PyPi User Strikes Again with Typosquatting, StarJacking and Unpacks Tailor-made Malware written in C#
 August 14, 2022
August 14, 2022
Typosquatting Campaign Targeting Python’s Top Packages, Dropping GitHub Hosted Malware with DGA Capabilities
 August 3, 2022
August 3, 2022
Large Scale Campaign Created Fake GitHub Projects Clones with Fake Commit Added Malware
 June 29, 2022
June 29, 2022
Amazon Confirmed and Fixed a High Severity Vulnerability of Broken Authentication in Amazon Photos Android App
 March 7, 2022
March 7, 2022
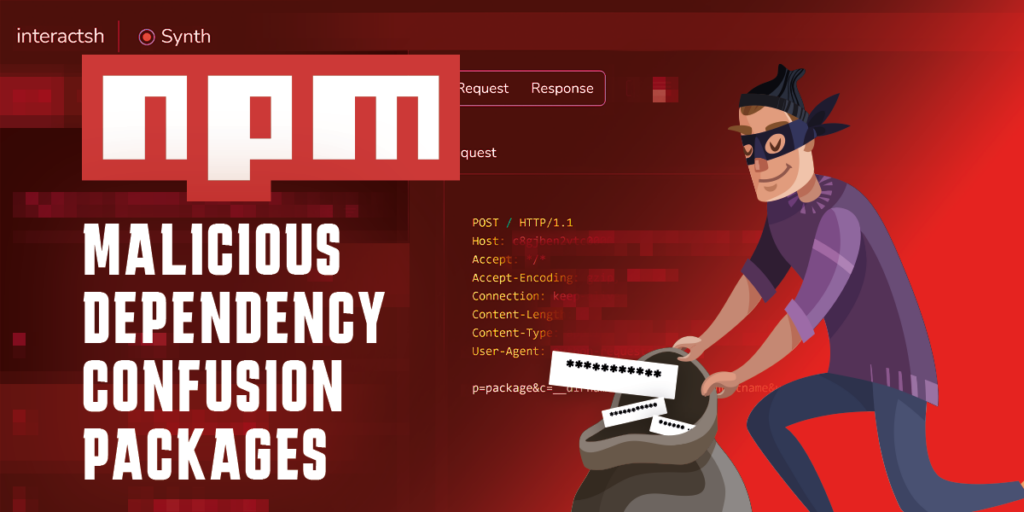
Webhook Party – Malicious packages caught exfiltrating data via legit webhook services
 February 8, 2022
February 8, 2022
Our Response to NPM Account Takeover Attacks – ChainAlert, a Community-Backed Open Source Tool
 December 28, 2021
December 28, 2021
CVE-2021-44832 – Apache Log4j 2.17.0 Arbitrary Code Execution via JDBCAppender DataSource Element
 June 14, 2021
June 14, 2021
CVE-2021-33829: Stored XSS Vulnerability Discovered in CKEditor4 Affects Widely-Used CMS
 February 11, 2021
February 11, 2021
Assistance Required: XSS Vulnerability Discovered in Helpdesk Software Solution Deskpro
 February 19, 2020
February 19, 2020
Checkmarx Research: Apache Dubbo 2.7.3 – Unauthenticated RCE via Deserialization of Untrusted Data (CVE-2019-17564)