
Over a thousand packages and users were created on NPM using an automated process in the past few days. Is it a phase one of an upcoming attack?
Checkmarx SCS team detected over 1200 npm packages released to the registry by over a thousand different user accounts. This was done using automation which includes the ability to pass NPM 2FA challenge. This cluster of packages seems to be a part of an attacker experimenting at this point.
We dubbed this new actor “CuteBoi” as a tribute to the “cute” username hardcoded in many of the packages’ configuration files and to one of the non-random NPM usernames the Attacker is using, “cloudyboi12”
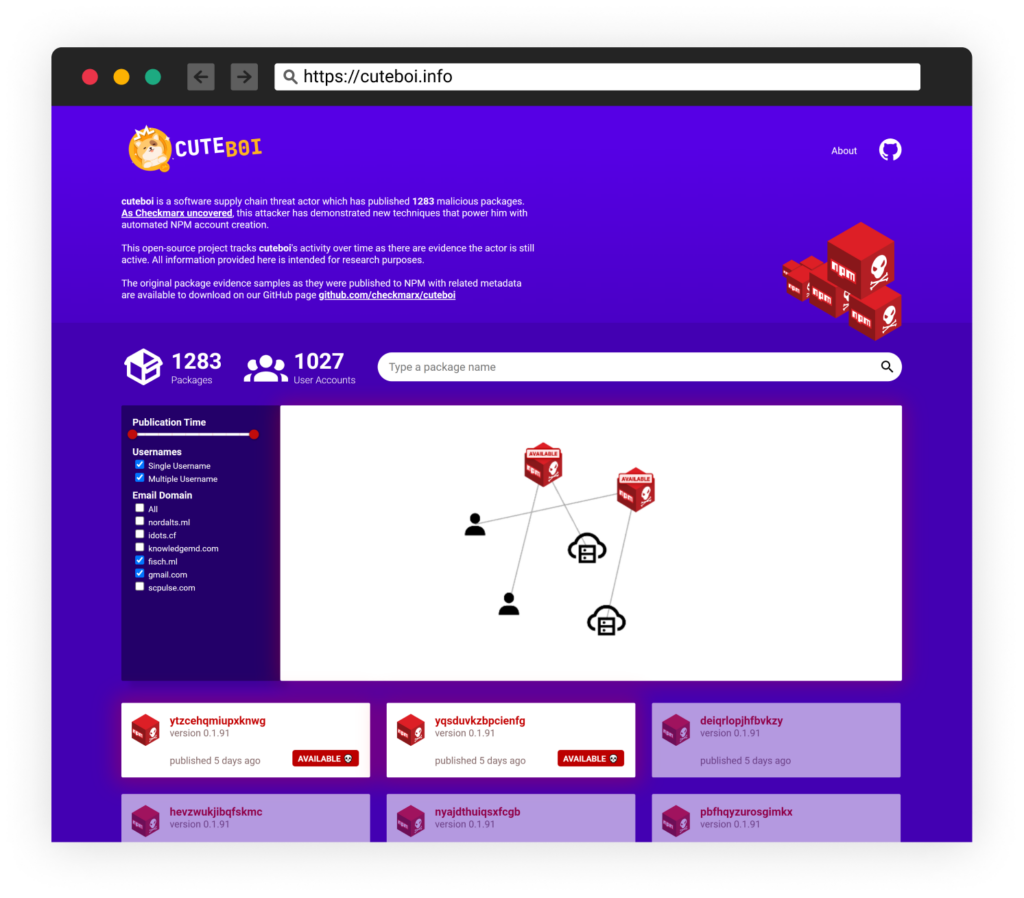
We expect this actor to continue their experimentation and eventually launch an attack that might cause real damage. Therefore, we have signed several traits of this Attacker’s behavior and continue to track them. The findings will be available to all on our dedicated tracker page cuteboi.info.
Details
In the past few days, Checkmarx SCS team detected a burst of suspicious NPM users and packages automatically created. All of these packages contain an almost identical duplicate of the code of the eazyminer package, a JS wrapper around XMRig. This wrapper was designed to utilize unused resources of machines such as ci/cd and web servers.
This suspicious activity includes over 1200 packages, of which more than 1000 are still available on the NPM registry. These packages were published by close to 1000 automatically created users.
At this point, downloading and installing these packages will have no negative effect on the machine. The copied code from eazyminer includes a miner functionality intended to be triggered from within another program and not as a standalone tool. The Attacker didn’t change this feature of the code and for that reason, it won’t run upon installation.
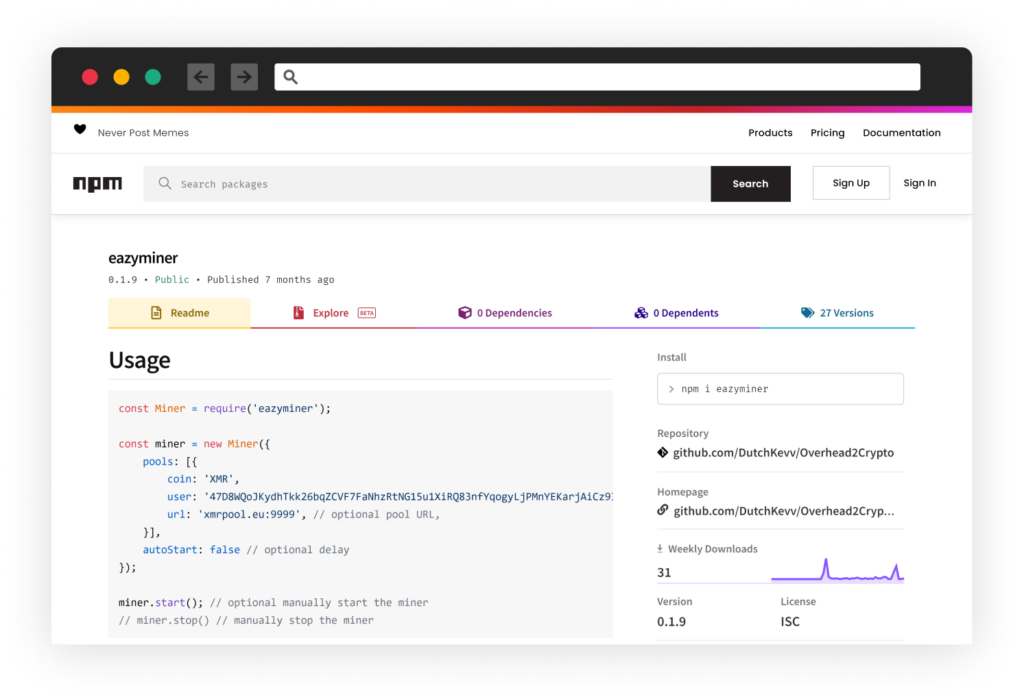
The original eazyminer usage instruction
CuteBoi did, however, make some changes in the miner’s configuration files. The most interesting of them is the URL to which the mined cryptocurrency should be sent, most likely running XMRig-proxy.
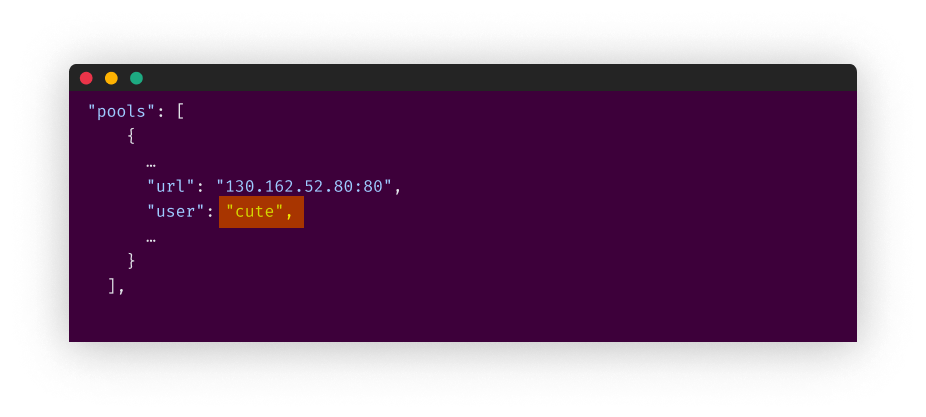
Known miners
At the heart of these packages are the XMRig miners. Their binaries, compiled for windows and linux systems, are shipped along with the packages. The Attacker changes the names of these binaries to match the random names of the package themselves.
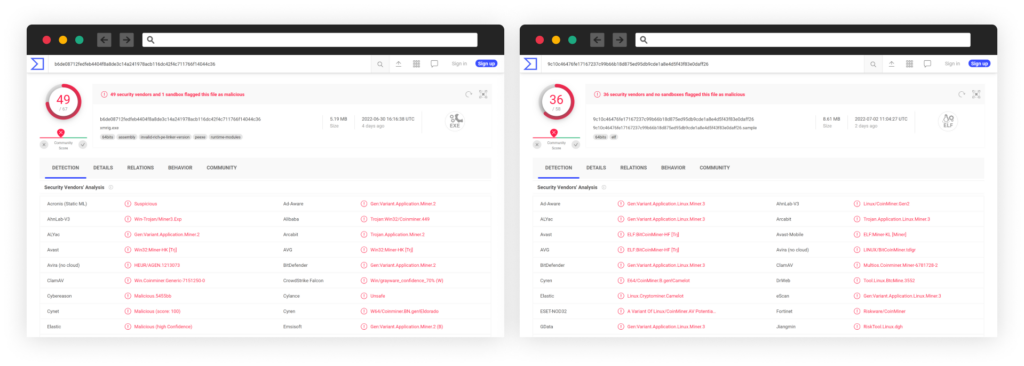
Automated Users Creation
CuteBoi is using automation to launch malicious packages at scale where almost every package being published has a unique NPM account, created using custom built automation processes.

Such automation technique was seen before with the threat actor RED-LILI where we saw the attacker launch a self-hosted server to support such automation. However, it seems that in this case, CuteBoi found a way to launch such attack without hosting a custom server and registering domains.
Fake Identity as-a Service
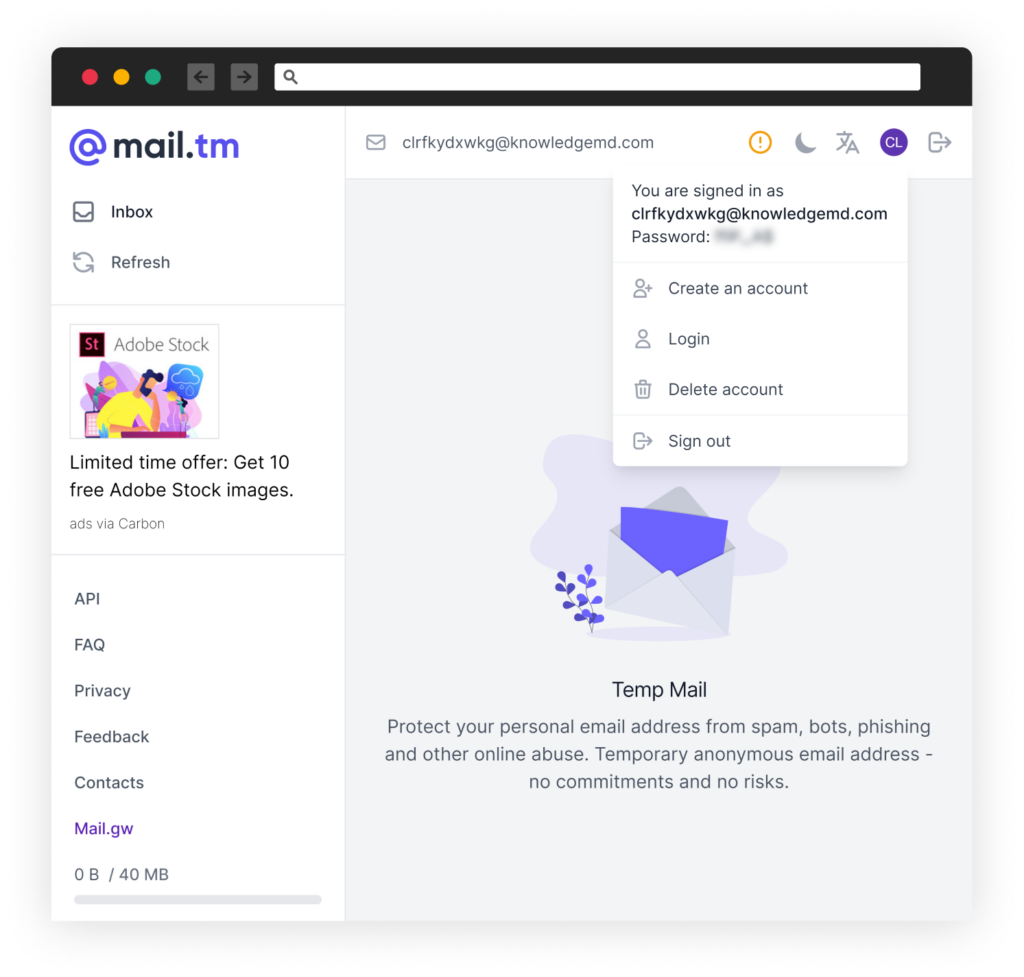
Looking at the domains with which CuteBoi is creating NPM users, we can deduce that they are using mail.tm – a free service providing disposable email addresses with REST API, enabling programs to open disposable mailboxes and read the received emails sent to them with a simple API call. This way CuteBoi can and easily defeat NPM 2FA challenge when creating a user account.
Sharing our Findings
As defenders we strongly believe in the power of sharing our findings publicly to help researchers improve their detection method and learn from real examples.
As a step to help the community, we’ve launched a tracker project called CuteBoi Tracker also available on GitHub where all information related to this attack group is shared and updated.
Conclusion
CuteBoi is the second attack group seen this year using automation to launch large-scale attacks on NPM. We expect we will continue to see more of these attacks as the barrier to launce them is getting lower.
We encourage open source developers to stay vigilant and check that they are not affected by this attack.
To stay updated on this actor’s activity, visit our tracker site cuteboi.info.
IOCs
- knowledgemd[.]com
- scpulse[.]com
- idots[.]cf
- fisch[.]ml
- Nordalts[.]ml
- 130.162.52[.]80
- XMRig Windows version
- 105704d5455bb188ad4985d5e593ff6c
- e22a630f3d3c7a78dbb47f44343b49059f98a251
- b6de08712fedfeb4404f8a8de3c14a241978acb116dc42f4c711766f14044c36
- d3e4daa6c4d5ec23f322a19dae173bd9
- c72dce5b747261a658a46d977a0b37ca628571f2
- 9c10c46476fe17167237c99b66b18d875ed95db9cde1a8e4d5f43f83e0daff26