
The newly discovered CVE-2022-42889 made some headlines recently. In this short blog we will discuss what the vulnerability is, its impact, and mitigation.
The package affected by the CVE is Apache Commons Text, an open-source Apache library that is “focused on algorithms that are applied to strings” (string substitution, lookups, matching and other algorithms). The discovered vulnerability exists throughout versions 1.5 to 1.9 and may lead to arbitrary code execution when untrusted data is processed and interpolated.
Executive Summary
A new vulnerability, CVE-2022-42889, commonly referred to ‘text4shell’, is a critical severity vulnerability affecting the popular Apache Commons Text. It is reminiscent, at its technical core, of the now infamous Log4Shell vulnerability – by processing values in a way that would allow invoking internal functionalities, which could, in turn, result in execution of arbitrary malicious code.
Fortunately, not all users of this library would be affected by this vulnerability – unlike Log4J in the Log4Shell vulnerability, which was vulnerable even in its most basic use-cases. Apache Commons Text must be used in a certain way to expose the attack surface and make the vulnerability exploitable.
Regardless, this vulnerability is severe, and users should make the effort to update this library to its latest version as soon as possible.
Technical details
In the Apache Commons Text, there is a feature that expands the text with lookups. Functions like replacing a string will call the vulnerable lookup function. This functionality is an implementation of a very basic expression language, which allows invoking several methods from within the interpolated string.
The lookup has number of fields which it tries to identify as shown below:
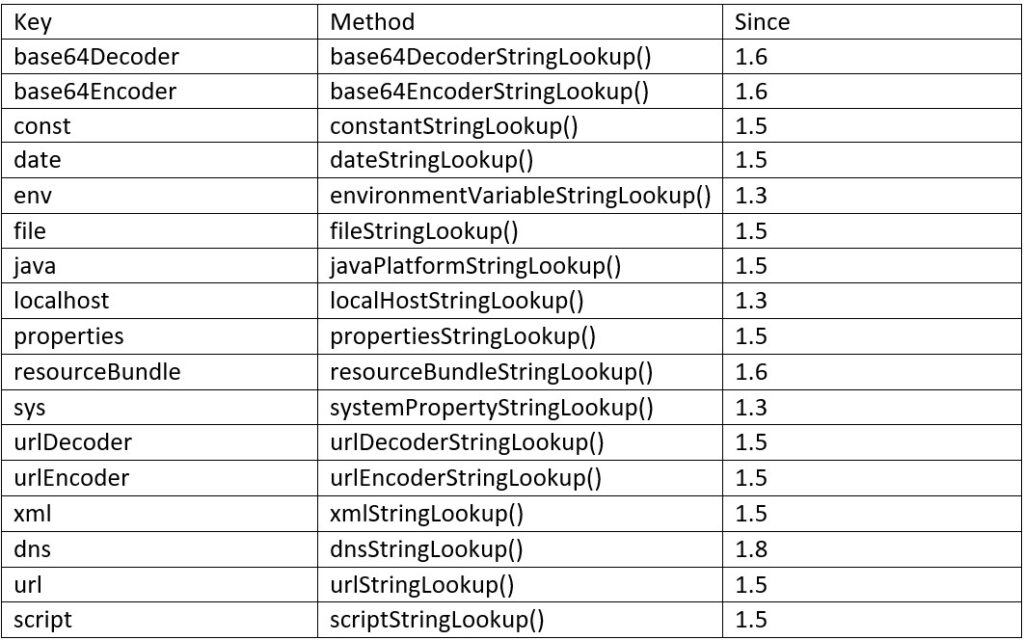
The fields that introduce security threats are the dns, url, and script − the worst one being script which opens the door for Arbitrary Code Execution. Using the ‘replace’ function, we can invoke a lookup with the expression language string ‘${<lookup field>:<lookup string>}’
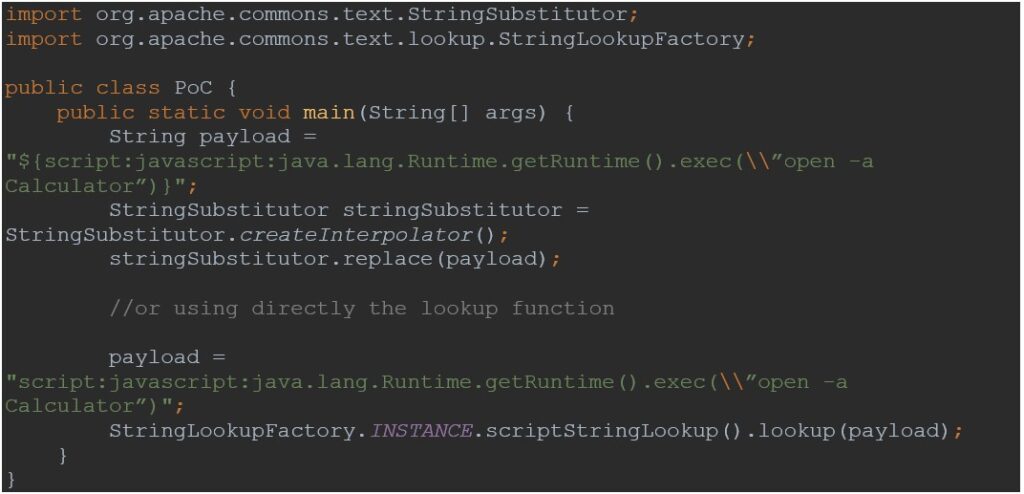
The following PoC uses the replace function with the payload containing the symbols “${}” for the lookup to execute. The second part of the code demonstrates invoking the lookup directly.
Log4Shell vs. CVE-2022-42889
When first seeing this vulnerability, we immediately associate it with Log4shell, hence the similar name, Text4shell (despite having nothing to do with the number 4). String interpolation of basic EL invoking code, with similar file names in (e.g. StringSubstitutor.java), invoking potentially dangerous methods are all very much reminiscent of Log4Shell. Despite the many resemblances to the infamous CVE-2021-44228, however, we must point out that the vulnerable package and functions is not as widely used in the wild. Another major difference is in implementation. While the most fundamental use-cases of Log4j were vulnerable in Log4Shell, this vulnerability requires an implementation pattern that may not affect all of its users.
Regardless, this vulnerability is significant, and the potential impact remains the same as unauthenticated RCE (remote code execution) is the most impactful attack one can have.
Remediation
The fix applied by the Apache team was the removal of the dns, script, and url lookups from the default interpolator behavior. In the StringLookupFactory.createDefaultStringLookups() method the DefaultStringLookup.DNS, DefaultStringLookup.URL and DefaultStringLookup.SCRIPT are now not added by default. In the previous versions, all the DefaultStringLookup instances were added by default.
The recommended action is to upgrade the package to the fixed version (1.10.0).
In case an upgrade is not possible, the StringSubstitutor can be initialized with safe StringLookup configurations.
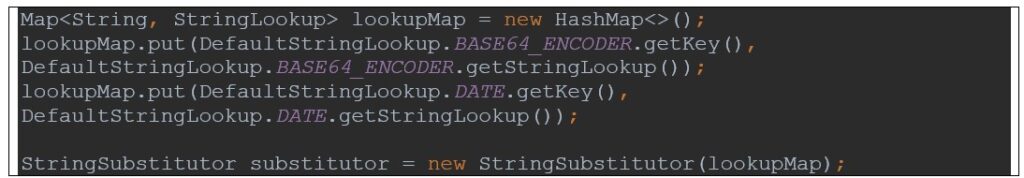
If the dangerous lookups are necessary in the application, all user input should be sanitized before being interpolated. A possible solution can be the use of a whitelist in the input validation phase.
Conclusion
In conclusion, the vulnerability may cause some panic in the wake of Log4shell. Despite it being less used in the wild, and despite requiring specific implementation for exploitation to be viable, it is still an important vulnerability since it is easy to exploit where vulnerable, it is widely used, and has significant impact. Checking if your code is vulnerable is highly important.
Checkmarx SCA customers can scan their code for similar types of vulnerabilities and get the latest remediation guidance.
Timeline
- 2022-03-09: Issue reported to security@commons.apache.org
- 2022-03-25: Apache Commons security team acknowledged receiving the report
- 2022-05-27: GHSL requested a status update
- 2022-05-27: Apache Commons security team notifies they are working on disabling the script interpolation by default
- 2022-06-29: Apache Commons security team states that “Commons Text” will be updated, in order to make the programmer’s intention completely explicit on using a “dangerous” feature
- 2022-08-11: GHSL requested a status update
- 2022-10-12: Apache Commons Text releases version 1.10.0 where script interpolation is disabled by default