
Containerization has transformed software development by boosting portability and deployment efficiency. However, this shift also brought substantial security challenges. Unlike traditional monolithic apps, containers create a dynamic and distributed environment that expands the potential attack surface.
By 2029, more than 95% of global organizations will be running containerized applications in production, according to Gartner. This is a significant increase from less than 50% in 2023. To address these challenges, Checkmarx has developed an innovative container security solution designed to secure your applications from development to deployment.
Let’s explore the real-world impact of our solution and highlight how it helped a leading cloud-based service provider enhance their own container security.
But first…What are containers
Containers are a type of virtualization technology that packages an application and its dependencies together. This allows the application to run consistently across different computing environments, regardless of the underlying operating system. In simpler terms, imagine a container as a shipping container – it carries everything an application needs to run (code, libraries, settings), but remains isolated from the system it runs on (like the operating system on a server). This isolation ensures portability and security for the application.
While containers provide many benefits, they also introduce unique security challenges. For example, pulling container images from public registries can expose systems to malware and vulnerabilities. Using large base images is like carrying unnecessary baggage—they slow down operations and introduce extra vulnerabilities and limited visibility in managing containerized environments can hide security threats.
Containerization is popular when developing, deploying, and running microservices-based applications. Microservices are small, independent applications that work together to form a larger application. Containers are ideal for this because they isolate each service and make them easy to deploy and scale. Because containers offer efficient resource utilization and faster deployment times, it is easier for developers to build, test, and deploy applications rapidly.
Why securing containers is crucial
We know that it’s convenient to pull container images from public registries. Although it saves time, this practice can expose your systems to malware and vulnerabilities, since hackers often upload malicious images to exploit unsuspecting developers. Similarly, sensitive information like passwords or API keys can inadvertently find their way into container registries, leading to data breaches. Managing these secrets is crucial.
Another pitfall is relying solely on static image scanning tools. These tools are great for detecting known vulnerabilities, but often miss emerging threats or misconfigurations. This oversight can leave your containers exposed. The inherent nature of containers increases the attack surface compared to traditional applications. Developers must secure multiple layers, including container runtimes, orchestrators, and plugins, to mitigate these risks effectively.
Adopting minimal base images, updated regularly, can significantly reduce these risks. Limited visibility makes it challenging to detect and respond to issues in real time. Robust visibility and observability tools are essential in gaining deep insights into container workloads and implementing effective threat detection and response strategies.
While containers offer immense benefits, they also require security frameworks. Addressing issues like insecure image sources, exposed secrets, incomplete static scanning, an increased attack surface, bloated base images, and limited visibility can help secure your containerized environments. Staying ahead of threats ensures that you can harness the full potential of containerization without compromising on security.
Introducing our new Container Security solution
Checkmarx provides a new powerful container security solution that enhances team efficiency across the software development lifecycle. It empowers developers and security teams with the following benefits:
Comprehensiveness: Checkmarx goes beyond static scanning, offering a rich set of features including image scanning, package inspection, vulnerability assessment, triage, remediation, results view, scan risk report, image breakdown, and Sysdig integration for runtime coverage.
Proactive Security: Early vulnerability identification and mitigation within the development process minimizes security risks in production.
Actionable Insights: Checkmarx provides detailed information about vulnerabilities, enabling developers to prioritize remediation efforts and act.
Ease of Use: The solution integrates seamlessly with existing workflows, minimizing disruption to development processes.
Diving into key container security capabilities
Let’s dive into some of our key container security capabilities:
Checkmarx’ container security approach starts with comprehensive image scanning. It examines every layer of an image—base image, software dependencies, and application code—to uncover vulnerabilities and threats. Constant updates to vulnerability databases ensure it identifies the latest threats.
Next, the solution inspects packages within container images. It performs checks like version control to confirm the use of latest secure versions and verifies licenses to avoid potential legal issues.
Finally, it offers detailed image breakdowns. Users can drill down into each layer of a container image to view vulnerabilities and package details. This granular view enables developers to pinpoint andaddress specific security issueseffectively.
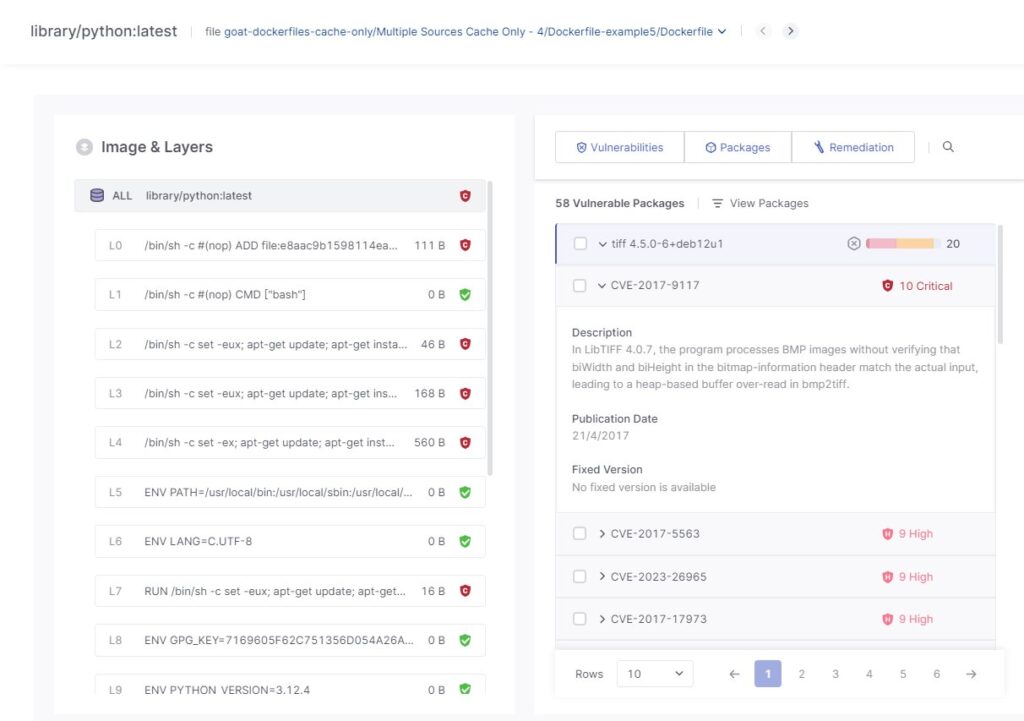
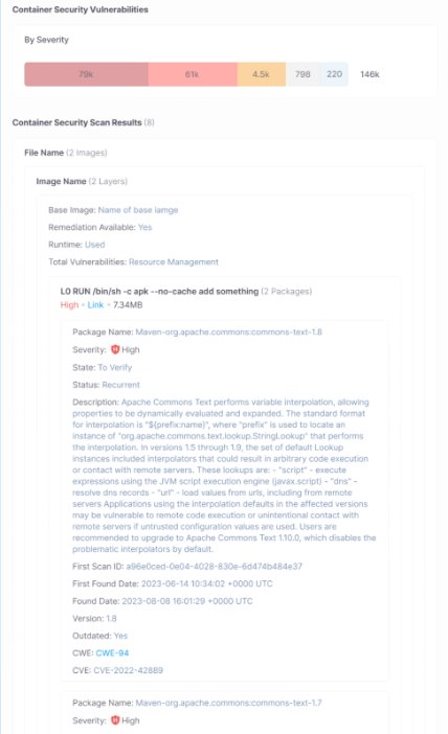
Vulnerability Assessment: Checkmarx prioritizes vulnerabilities based on severity and provides detailed information about each one. This includes the CVE details, potential impact, and remediation guidance.
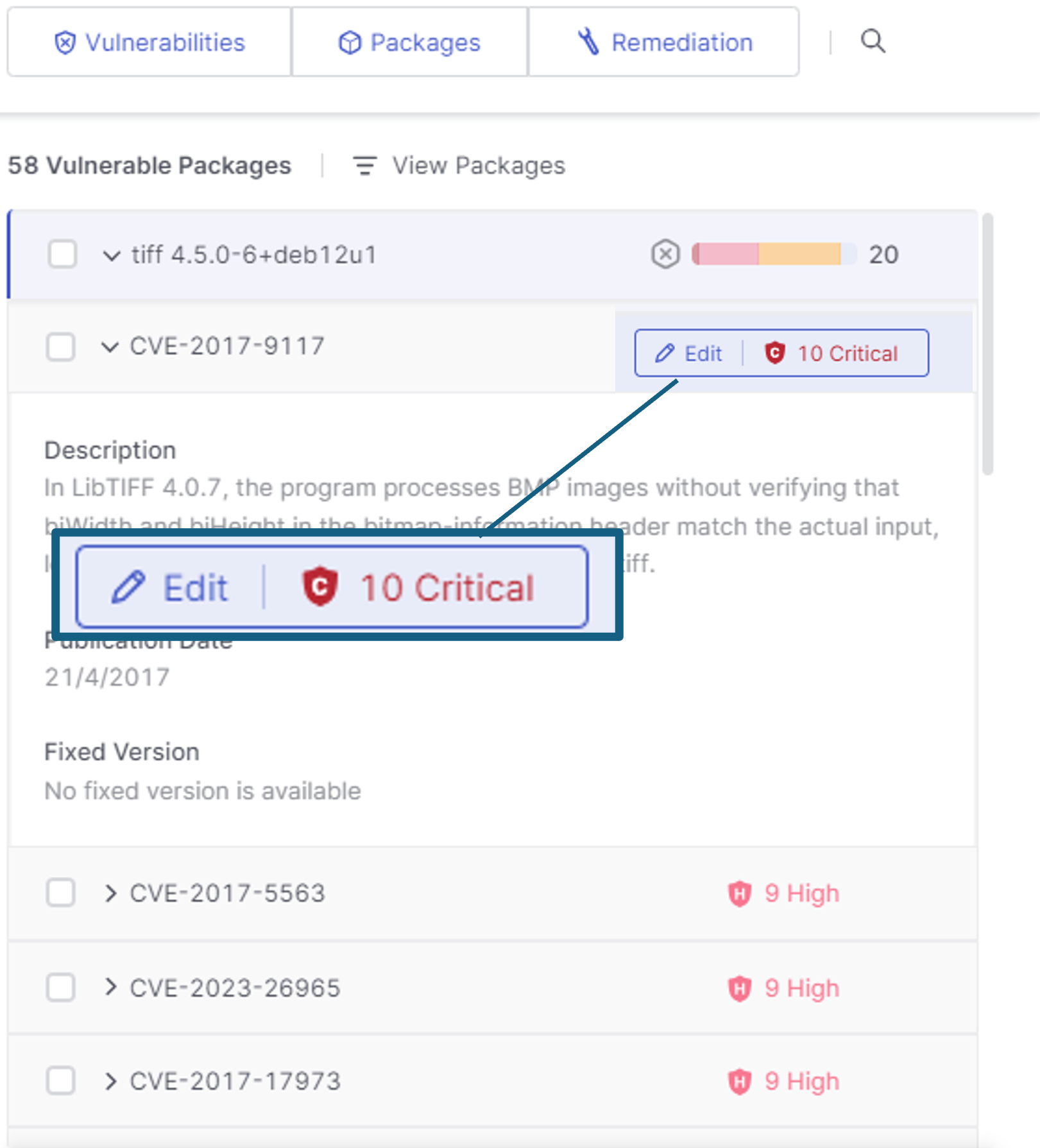
Triage: This allows users to manage the severity, and status, of vulnerabilities for each project or application. They can update severity levels, change status (e.g., Verify, Not Exploitable), and maintain detailed audit trails for all actions taken.
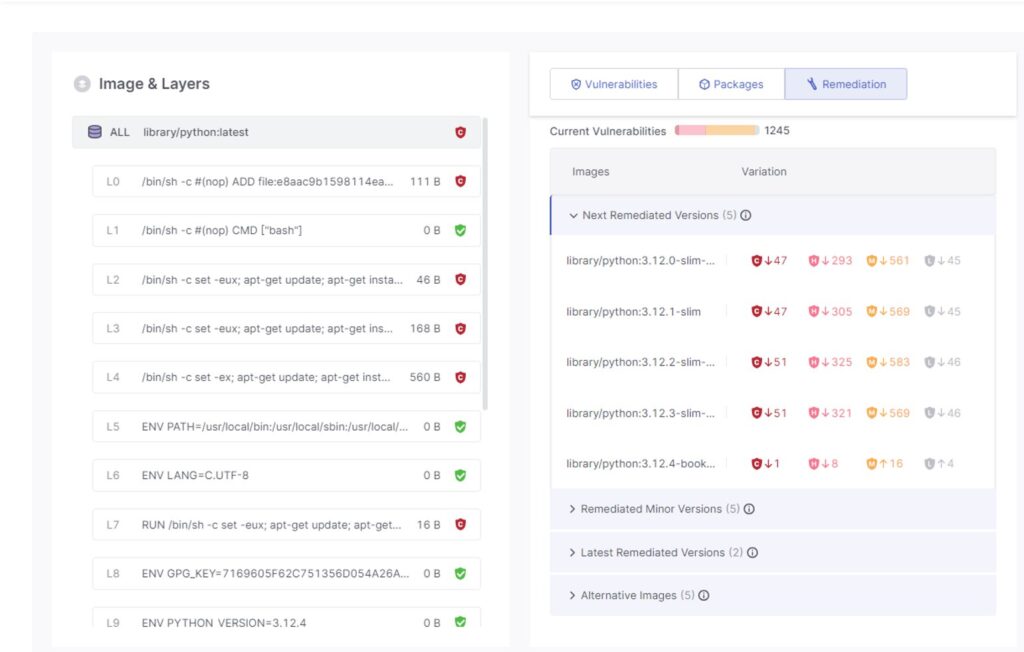
Remediation: Checkmarx identifies vulnerabilities within container images and recommends alternative base images with a lower security risk profile. This approach helps developers choose more secure foundations for their applications.
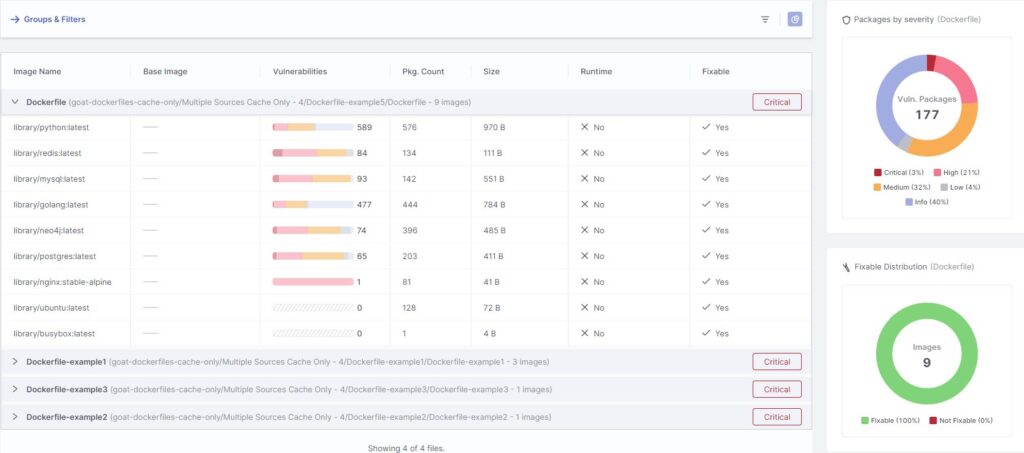
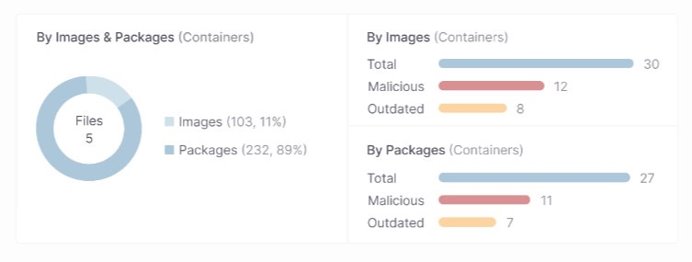
Results View: This intuitive interface provides a detailed view of container image scan results. Users can see the distribution of vulnerabilities across different severities and analyze them based on runtime status.
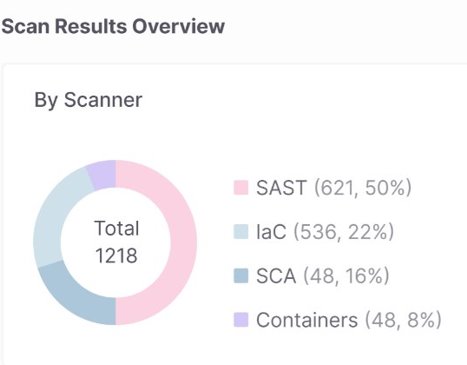
Scan Risk Report: Checkmarx generates comprehensive reports summarizing scan results, including the number of vulnerabilities and their severity. These reports can be downloaded in various formats (JSON, CSV, PDF) for further analysis and compliance purposes.
Final Thoughts
Checkmarx offers a comprehensive container security solution that empowers developers and security teams throughout the development lifecycle. By identifying and mitigating vulnerabilities early, Checkmarx helps organizations build secure and compliant containerized applications. The case study demonstrated how a cloud service provider achieved a significant reduction in vulnerabilities and improved security posture with Checkmarx.
As containerization continues to reshape software development, prioritizing container security is no longer optional. By leveraging solutions like the Checkmarx One Platform, organizations can unlock the full potential of this technology while ensuring the long-term security of their applications and data.
Ready to take the next step?
Visit our website to learn more about Checkmarx’s container security solution and download our free container security Enhancement guide. You can also request a demo to experience the solution firsthand and see how it integrates seamlessly into your development workflow.
Wondering what you should consider when picking a container security solution? These are six things important things you should keep in mind.
Glossary of terms – Container Security
Attack Surface: The sum of all potential entry points that an attacker can use to gain access to a system. A larger attack surface means more vulnerabilities attackers can exploit.
Base Image: The foundation image upon which a container is built. It typically contains the operating system and essential libraries needed for your application to run. Choosing a minimal base image reduces the attack surface.
Container: A lightweight, self-contained unit of software that packages code and all its dependencies (libraries, configuration files) for deployment and execution. Imagine a shipping container for code, allowing it to run consistently across different environments.
Container Image: A template that defines the contents and configuration of a container. It’s like a blueprint for building a container with specific functionalities.
Container Registry: A repository that stores and manages container images. Developers can pull (download) images to create containers and push (upload) new images they’ve built. Think of it as a library for container images.
Container Security: The practice of protecting containerized applications and the infrastructure they run on from vulnerabilities, malware, and unauthorized access. It’s crucial to ensure the integrity and security of your containerized environment.
DevSecOps: An approach to software development that integrates security considerations throughout the entire development lifecycle (Dev), security operations (Sec), and IT operations (Ops). Container security is a key aspect of DevSecOps.
Exploit: A piece of code or script that takes advantage of a vulnerability to gain unauthorized access or cause harm. Exploiting vulnerabilities in containers can compromise your applications and data.
Runtime: The environment where containers are executed. Container security needs to consider both the security of the image and the runtime environment.
Static Image Scanning: A security analysis technique that examines container images for known vulnerabilities without running the container. It’s like checking the ingredients list of a meal for potential allergens before cooking.
Vulnerability: A weakness or flaw in software that can be exploited by attackers to gain unauthorized access or cause harm. Vulnerabilities in container images or underlying infrastructure pose a risk to container security.