
Research by Yehuda Gelb and Tzachi Zornstein
A malicious campaign involving several python packages, most notably the “spl-types” Python package began on June 25th with the upload of an innocuous package to PyPI. This initial version, devoid of malicious content, was intended to establish credibility and avoid immediate detection. It was a wolf in sheep’s clothing, waiting for the right moment to reveal its true nature. The attacker’s patience paid off on July 3rd when they unleashed multiple malicious versions of the package. The heart of the malware was in the init.py file, obfuscated to evade casual inspection. Upon installation, this code would execute automatically, setting in motion a chain of events designed to compromise and control the victim’s systems, while also exfiltrating their data and draining their crypto wallets.
Key Findings
- Multiple malicious Python packages were uploaded to PyPI, targeting cryptocurrency users involved with Raydium and Solana.
- The attacker exploited StackExchange as their primary vector to direct people to their malicious package. They posted a seemingly helpful answer on a popular thread that referenced their malicious package, leveraging trust in community-driven platforms.
- The multi-stage malware exfiltrated extensive sensitive data and facilitated the draining of victims’ crypto wallets
- Windows Virus and Threat Protection failed to detect the active malware on a victim’s system, providing a real-world validation of our previous research demonstrating that modern EDR systems are ineffective against threats from malicious packages.
- A backdoor component in the malware granted the attacker persistent remote access to victims’ systems, enabling potential future exploits and long-term compromises.
A Multi-Stage Assault
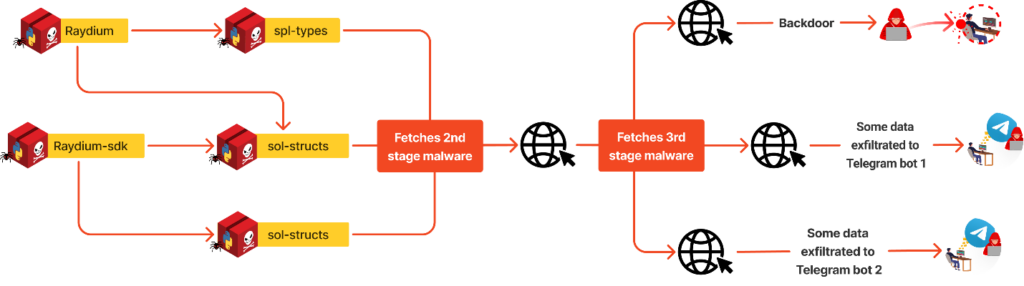
The initial payload acted as a springboard, reaching out to external resources to download and execute additional malicious scripts. These scripts formed the core of the operation, and meticulously scanned the victim’s system for valuable data. The malware cast a wide net, targeting an array of sensitive information – browser data was readily available, as the malware harvested saved passwords, cookies, browsing history, and even stored credit card information. Cryptocurrency wallets, including popular options like Exodus, Electrum, and Monero, were also prime targets. The attack didn’t stop there; it also sought out data from messaging applications such as Telegram, Signal, and Session. In a particularly invasive move, the malware captured screenshots of the victim’s system, providing the attacker with a visual snapshot of the user’s activities. It also scoured the system for files containing specific keywords related to cryptocurrencies and other sensitive information, including GitHub recovery codes and BitLocker keys. The final part of this digital heist involved compressing the stolen data and exfiltrating it to the attacker’s command and control server via several Telegram bots.
Also included in the malicious scripts was a backdoor that granted the attacker remote control over the victim’s system, allowing for ongoing access and potential future exploits.
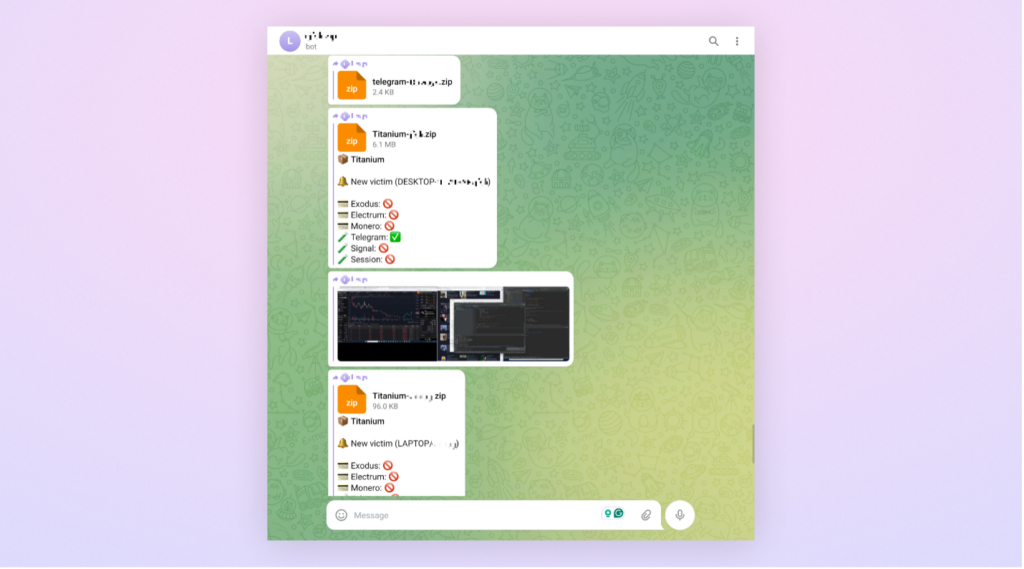
One of the attacker’s telegram bots receiving screenshots and data from victims machines.
Profiling the Victims & Motives behind the attack
As we continued to follow this attack, a clear pattern emerged around the victims. What united them was not their profession or location, but their involvement with Raydium and Solana, two prominent players in the cryptocurrency space. This commonality suggests that the attacker had a specific target in mind.
The focus on users of these platforms indicates a level of strategic thinking on the part of the attacker. By targeting this specific group, they positioned themselves to potentially intercept or manipulate high-value transactions, pointing to clear financial motives behind the attack.
Delivery Strategy of the Malware
The attacker was strategic when thinking about how to deliver the malicious package to unsuspecting victims. Their approach was twofold: create a seemingly legitimate package and then lending it credibility through manipulative online engagement.
Step 1: Crafting a Deceptive Package
The first step involved creating a package that would raise minimal suspicion.
In screenshots from compromised systems, we observed victims using, or installing, a package named “Raydium”.
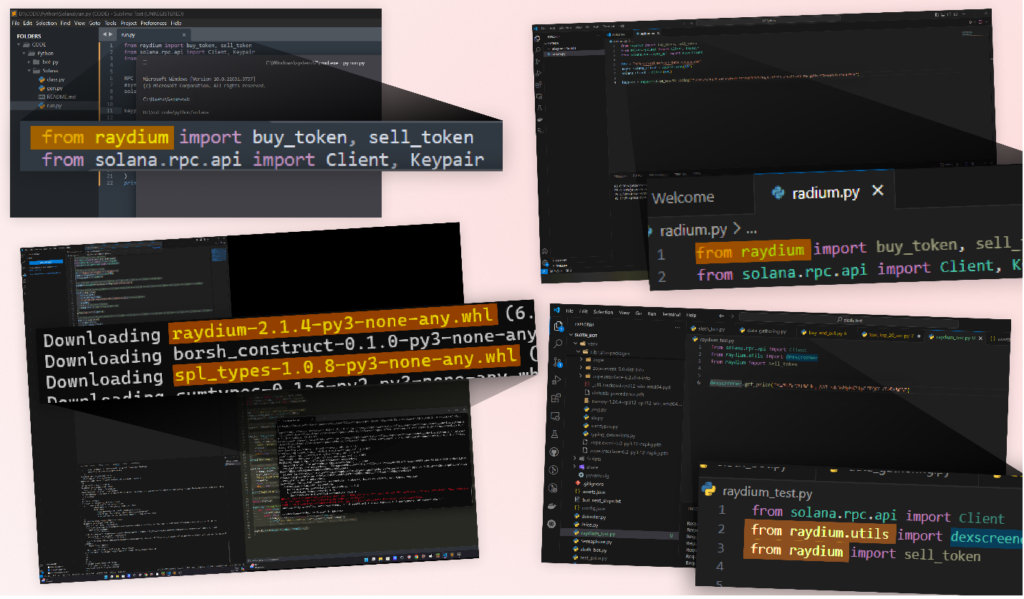
It’s crucial to note that while Raydium is a legitimate blockchain-related platform (an Automated Market Maker (AMM) and liquidity provider built on the Solana blockchain for the Serum Decentralized Exchange (DEX)), it does not have an official Python library.
Exploiting this gap, the attacker, used a separate username to publish a Python package named “Raydium” on PyPI.
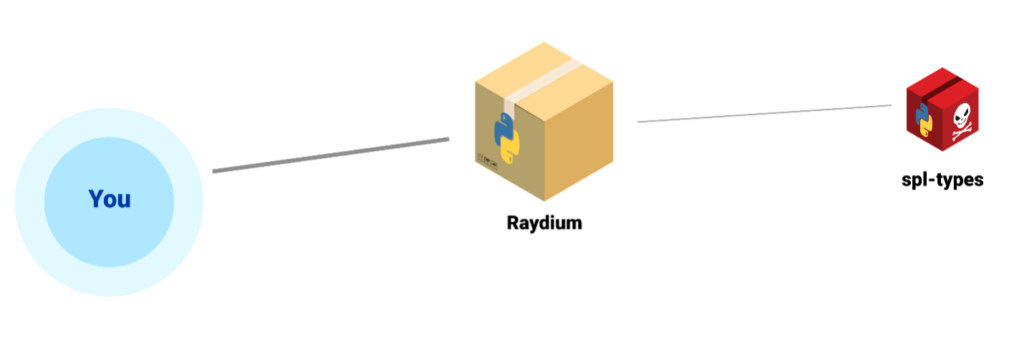
The malicious packages of this campaign were dependencies within other seemingly legitimate packages.
This package included the malicious “spl-types” as a dependency, effectively disguising the threat within a seemingly relevant and legitimate package.
Step 2: Building Credibility and Ensuring Adoption
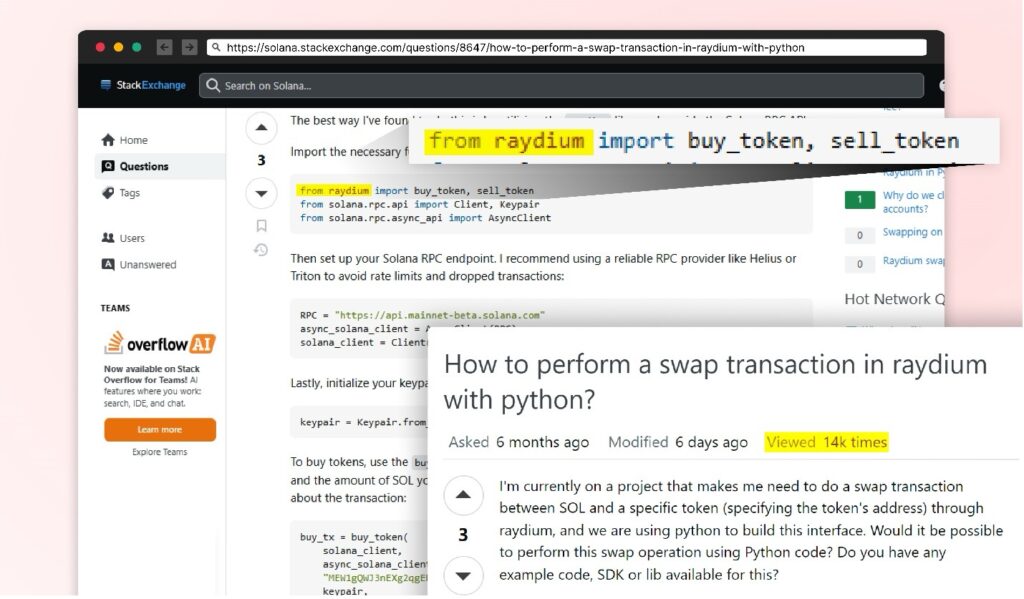
To lend credibility to this package and ensure its widespread adoption, the attacker scoured StackExchange, a popular Q&A platform similar to Stack Overflow, for highly viewed threads related to Raydium and Solana development. Upon identifying a suitable and popular thread, the attacker contributed what seemed to be a high-quality, detailed answer. This response, while ostensibly helpful, included references to their malicious “Raydium” package. By choosing a thread with high visibility—garnering thousands of views—the attacker maximized their potential reach.
Developers seeking solutions to Raydium-related questions would likely view the answer as credible and follow the suggestions with minimal suspicion.
This tactic underscores the importance of verifying the authenticity of packages, especially those recommended in forums by unknown individuals.
Case Studies and the personal impact
The impact of this attack goes beyond theory. Behind each compromised system is a real person, and their stories reveal the true cost of such breaches. There were many cases, but in this blog, let’s look at a couple notable ones that highlight different aspects of this attack:
Case Study 1
In one of the malware-captured screenshots, we observed clear personal details of a victim. Cross-referencing this information with LinkedIn allowed us to identify the individual, who happened to also be employed at a respected IT company. This discovery prompted us to take the step of reaching out to warn them about the breach. During our subsequent communication, we learned the victim’s entire Solana crypto wallet had been drained shortly after unknowingly downloading the malicious package. This case vividly illustrates how such attacks can have immediate and severe financial consequences for individuals.
Case Study 2
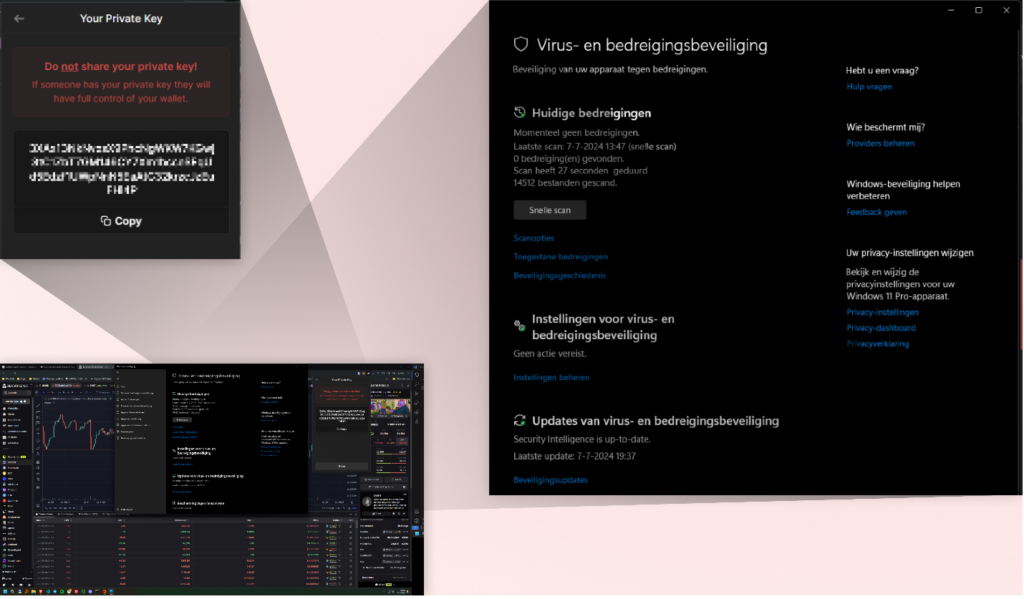
Bottom left: Screenshot of the victim’s screen. Top right: Windows Defender scan declaring in Dutch that the system is clear of threats after the scan. Top left: victim’s private key.
Another victim’s experience highlighted a critical weakness in current cybersecurity practices. A screenshot from their system showed a private key clearly visible – a goldmine for any attacker since these keys bypass any password or multi factor authentication active on the account that the private key is for.
In addition to that, and what made this image particularly alarming, was the Windows Virus and Threat Protection screen displayed alongside it, declaring that a scan had just been completed and that the system was clear of threats.
The revelation that Windows Virus and Threat Protection failed to detect the threat during active data exfiltration is particularly concerning. It emphasizes a critical blind spot in traditional security measures when it comes to malicious activities initiated through package managers. This failure of detection occurred not just before or after the attack, but during the very moment the malware was active and stealing data.
This incident provides a real-world example of how Endpoint Detection and Response (EDR) systems can fall short in stopping malicious package activity or sending relevant alerts.
Moreover, even if the malicious package is later taken down from the repository and not publicly declared as malicious, EDR systems typically won’t flag the package as vulnerable if it remains installed on a user’s system. This leaves users potentially exposed to ongoing threats from previously downloaded malicious packages.
PyPi for example, to this day, completely eliminates all traces of a package, leaving no placeholders behind. Although malicious usernames often remain, they appear without any associated malicious packages. Consequently, anyone who encounters these malicious usernames may be unaware of the user’s history of uploading malicious packages.
Just recently, we published a POC on the blind spots of current EDR solutions.
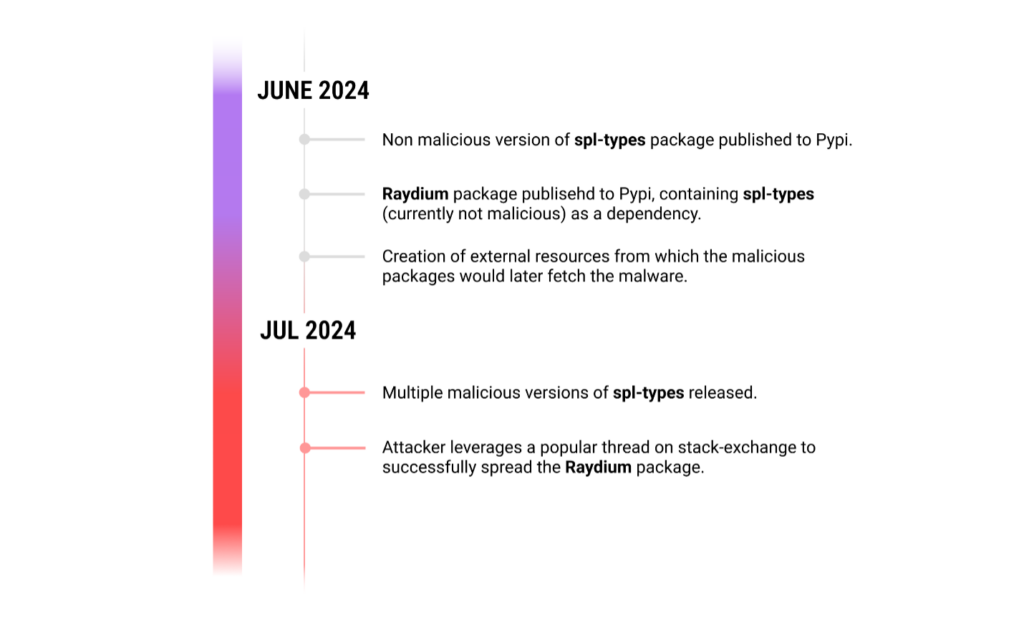
Attack Timeline
Conclusion
The “spl-types” malware incident is more than just another data breach. It serves as a stark reminder of the cost of cybersecurity failures and the ongoing challenges we face in securing the software supply chain.
This incident’s impact extends beyond individual users to enterprises. A single compromised developer can inadvertently introduce vulnerabilities into an entire company’s software ecosystem, potentially affecting the whole corporate network.
This attack serves as a wake-up call for both individuals and organizations to reassess their security strategies. Relying solely on traditional security measures is not sufficient. A more comprehensive approach is needed, one that includes rigorous vetting of third-party packages, continuous monitoring of development environments, and fostering a culture of security awareness among developers.
As part of the Checkmarx Supply Chain Security solution, our research team continuously monitors suspicious activities in the open-source software ecosystem. We track and flag “signals” that may indicate foul play and promptly alert our customers to help protect them.
The fight against such sophisticated threats is ongoing, and as we gather more insights into the attacker’s methods and infrastructure, we will continue to share our findings with the community. Together, we can work towards a safer digital future for all.
Packages
- spl-types
- raydium
- sol-structs
- raydium-sdk
- sol-instruct
IOC
- Hxxps[:]//ipfs.io/ipfs/QmQcn1grVAFSazs31pJAcQUjdwVQUY9TtZFHgggFBN6wYQ
- hxxps[:]//rentry[.]co/7hnvbc6n/raw
- hxxps[:]//api.telegram[.]org/bot6875598996:AAGATybCyN73i3als0VRGlP8cILsFjKf4ao/sendDocument?chat_id=7069869729
- 147[.]45[.]44[.]114
- hxxps[:]//api[.]telegram[.]org/bot7265790107:AAE9XT3b23WyBHq-0fw5BwW5U7wzYNZT3cc/sendDocument?chat_id=7069869729
- hxxps[:]//rentry[.]co/foyntbdk/raw
- hxxps[:]//api.telegram[.]org/bot7265790107:AAE9XT3b23WyBHq-0fw5BwW5U7wzYNZT3cc/sendPhoto?chat_id=7069869729
- hxxps[:]//rentry[.]co/xcsshmno/raw
- hxxps[:]//rentry[.]co/2p7kv9d8/raw