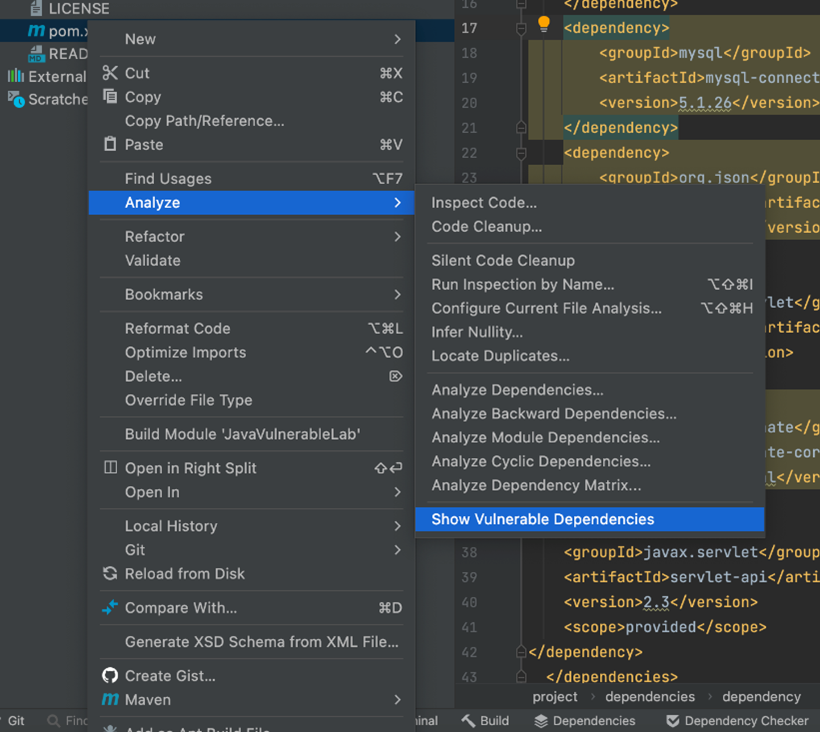
- IntellliJ IDEA v. 2022.1 and later bundle the free security plugin that identifies vulnerable packages
- Both declared and transitive packages are identified
- Beyond highlighting vulnerable packages, detailed information including suggested fixes is provided
The JetBrains IntelliJ IDEA now features the bundled JetBrains Dependency Checker plugin powered by Checkmarx. Dependency Checker identifies vulnerable packages which you directly or indirectly (transitive) include in your application code. Analyzing your code is a simple as right-click, selecting Analyze and Show Vulnerable Dependencies.
Don’t let the ease of activating plug-in deceive you – Dependency Checker plugin leverages a comprehensive threat intelligence database to help you overcome a major challenge – the volume and pace of delivery of security information about OSS.
As modern application development continues to drive the pace of application development, having more OSS code in the software stack of an application than proprietary code is now mainstream. As the part of your application which relies on external code, it is incredibly difficult to keep-up with the security status of all the open source software (OSS) packages that your applications rely on, especially when also considering transitive packages.
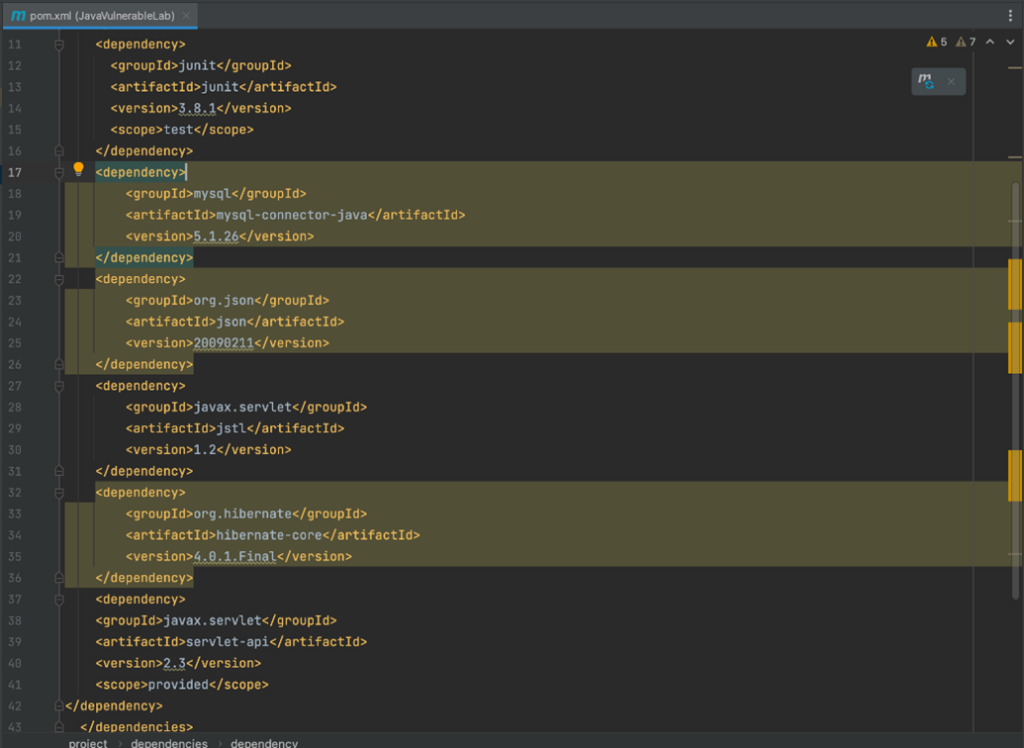
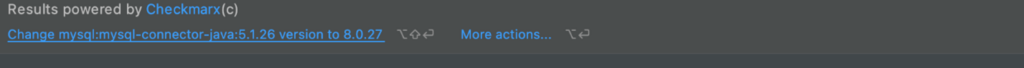
When active, Dependency Checker highlights vulnerable packages directly in IntelliJ IDEA, as illustrated in the screenshot below. Information about the vulnerabilities is equally easy to access with a couple of clicks. Curated information is drawn from public sources as well as proprietary Checkmarx research, ensuring that you are always on top of the latest information.
A different view displays all of the vulnerable packages in a project within their hierarchy, including transitive packages. The same area can also provide a flat view of either all packages or only vulnerable packages.
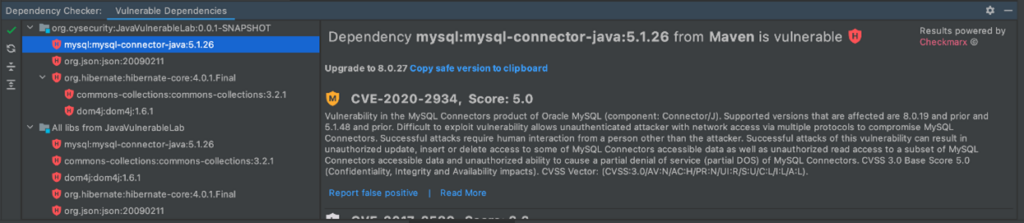
Beyond providing valuable security information, Dependency Checker also provides remediation information. Going a step further, developers can quickly take action to remediate, for example, moving to a safe version of the package.
This is all provided within the IDE, bringing Checkmarx security directly to where developers work. This approach eliminates friction introduced by having to cross reference between security and development tools.
The Dependency Checker functionality is drawn from some of the functionality of Checkmarx Software Composition Analysis (SCA). The broader solution is best leveraged by organizations with multiple developers, teams, and/or projects. The enterprise-grade features include Software Bill of Materials (SBOM) generation, centralized management and reporting, prioritization of vulnerabilities based on factors such as Exploitable Path (if and how the vulnerable code is actually used by the application), among other features. While these wider features are invaluable for organizations, the vulnerability information within the Threat Intelligence database as used by Dependency Checker is exactly the same as used and trusted by enterprises around the world.
Quite recently, Checkmarx SCA has been further enhanced with the inclusion of Supply Chain Security (SCS). Going beyond vulnerability information, SCS continuously analyzes information to look for anomalies in contributor reputation, package provenance, project health, and other indicators of software supply chain attacks in open source ecosystems. Unlike vulnerabilities which are almost always honest mistakes, supply chain attacks attempt to inject outright malicious code into your software supply chain, a concern of growing urgency for organizations everywhere.
The JetBrains IntelliJ Dependency Checker plug-in will help you quickly identify vulnerable OSS packages included in your applications, giving you core benefits of software composition analysis in the simplest possible delivery model. Go activate it in your IntelliJ IDEA!
Download our joint e-Book to find our more.
To get IntelliJ IDEA go here.
For some quick tips and other information, go here.
To explore more about SCA and get a free demo, go here.
If supply chain security piqued your curiosity, more information is here.