Summary
In the world of application security, malicious code is a growing issue, especially as developers start leaning on AI code-generating tools to speed up the pace of application development. In this article, we will look at what malicious code is, how malicious package protection works, and the best practices for implementing malicious code security strategies as part of a comprehensive application security solution.
What is Malicious Code?
Malicious code refers to any type of software or script intentionally designed to cause harm, exploit vulnerabilities, or compromise the integrity, confidentiality, or availability of a system. Malicious code can carry a wide range of cyber risks, including viruses and worms, ransomware, data exfiltration, and spyware. Malicious code may be delivered in the guise of a useful open source software (OSS) package that looks like it’s intended to perform a legitimate function, but in reality it is created to gain unauthorized access to your systems, steal data, disrupt operations, or even mine for Bitcoin using your resources.
What is Malicious Package Protection?
As malicious code is such a prominent threat, malicious package protection consists of the strategies, technologies and processes that enterprises use to safeguard their systems against any malicious software packages that may expose their business to risk.
In the context of application development, OSS packages are easily downloadable collections of pre-written code that developers use to quickly and easily add functionality to their applications. These packages are often sourced from widely used code repositories, which are easy to access, free of charge, and simple to customize – which is why they are increasingly popular with development teams. Popular repositories include GitHub Packages, npm, PyPI and NuGet Gallery.
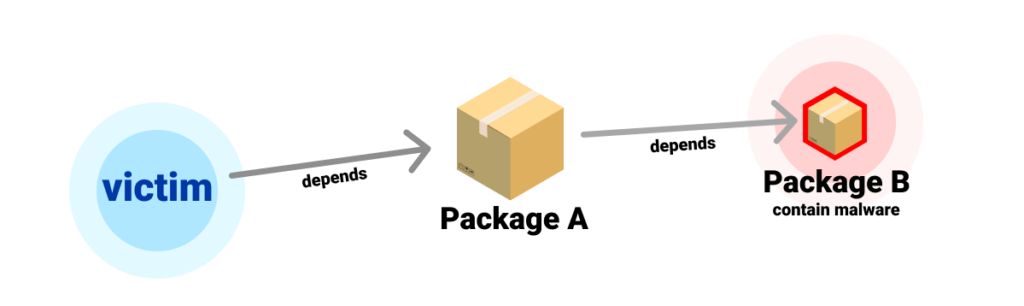
However, not all OSS packages are trustworthy; some contain malicious code intentionally inserted by a threat actor in order to perpetrate an attack.
Malicious package protection is about minimizing the risks of utilizing open source packages, and involves mechanisms such as automated scanning tools, dependency checks, manual research, and stringent validation processes to ensure that only safe and verified packages are used in software development. By implementing these measures, organizations can significantly reduce the risk of incorporating third-party code into their applications.
Why is Protection from Malicious Code Critical for Enterprises?
Protecting against malicious code needs to be a priority for enterprise CISOs, AppSec teams, and developers, as the implications of a security breach or sensitive data loss can be catastrophic. Not only will businesses have to handle the financial cost of downtime, business disruption, reputational damage, and lost customers, but there are often compliance ramifications as well, including penalties and legal fees.
Malicious code is also becoming more of a challenge in the era of open source collaboration, where developers want to increasingly rely on open source software packages such as Docker container images, Helm charts and Debian packages for example to speed up the pace of development or satisfy dependency requirements.
Key Considerations for Choosing an Effective Malicious Code Security Tool
When you’re thinking about how to implement security tools to protect against the presence of malicious code, it’s important to consider the role of the developer. The traditional friction between security and development teams stems from developers who don’t want security to feel like a hurdle in the way of their innovation and agility.
To solve this challenge, AppSec teams need to provide developers with a convenient way to secure against malicious code adoption, within the scope of their regular workflows. Even for developers without deep security expertise, an application security platform that offers security training, malware detection, and actionable remediation advice inside the developer’s Integrated Development Environment (IDE) can go a long way towards protecting the enterprise from malicious code, while empowering developers with the autonomy and agility that they want and need.
Another consideration is the concept of exploitability. Because development and security teams are drowning in a sea of security alerts, it’s crucial for a malicious package protection solution to prioritize discovered risks. Two highly effective ways to accomplish this are to analyze source code to determine which malicious code is being called (this is known as exploitable path analysis) and to contextually recognize which malicious code is actually being called at runtime (sometimes called cloud insights).
Checkmarx One Offers a Leading Malicious Package Protection Solution as Part of Wider Application Security
At Checkmarx, malicious code security is a crucial element of our application security platform, a core tenet of our Software Composition Analysis and Container Security capabilities, and a differentiated capability in its own right to help detect malicious packages as part of wider application security best practices.
To date, our multi-layered package analysis methodologies have identified more than 385,000 malicious packages and counting – using a combination of advanced scanning technologies and the expertise of our security research team.
Checkmarx One’s Malicious Package Protection module detects malicious packages wherever they appear, whether it’s in manifest files, in binaries, or in containers. We use transitive dependency scanning in malicious package detection, which means even when a malicious package is a dependency of a dependency, it will show up in scan results.
Through an integration with Sysdig, we incorporate runtime data to help take detection further and reveal the real-world exploitability of malicious packages. This allows for intelligent prioritization and remediation based on actual runtime usage, rather than channeling resources to where any malicious packages are present in an application, even where they are not in use and the risk level is lower.
Checkmarx also generates smart reliability metrics, rating the trustworthiness of each open-source package that is referenced in applications, using details such as legitimacy, behavioral integrity, and the reputation of the specific contributor. As a customer, you can define your own specific policies which take immediate effect when any malicious packages are detected. According to your business context you can have the system automatically send an alert to the appropriate stakeholders, prevent pull requests that include this package, or break a build entirely until the issue is remediated.
Looking to reduce the risk of malicious code in your applications, and empower developers to securely move with speed and agility? Learn more about malicious package protection by requesting a demo.