Software Composition Analysis (SCA) protects applications from open source risks. A dev-focused SCA approach enables AppSec professionals and CISOs to meet security and compliance requirements without causing friction with development teams. This is because it encourages effective security integration into the development workflow, the identification of both vulnerabilities and malicious packages, and minimization of irrelevant findings to reduce noise.
The article below is a guide for AppSec teams and CISOs looking to take a dev-focused approach to SCA. First, we detail common open source risks enterprises encounter. Then, we provide 12 practices to augment your SCA strategy while minimizing friction with developers. In the end, we include a checklist you can follow and dev-friendly tool recommendations.
Common Open Source Code Risks
Open source code is widely used by developers to accelerate development in a cost-effective manner. However, the nature of open source, including its wide availability and anyone’s ability to contribute, also introduce several security risks.
These include:
- Supply Chain Attacks – Attackers might attack open source repositories or build packages. For example, by injecting malicious code into packages, creating namesakes, and others. This can affect all downstream users.
- Vulnerabilities – Just like proprietary software, open source code can include unintentional vulnerabilities. When added to the enterprise’s application code, this introduces vulnerabilities that could be exploited. Vulnerabilities might be present in the added code or in the project’s dependencies. They might be the result of insecure coding, insufficient patching of vulnerabile code or the use of outdated versions.
- Misconfigurations – Open source projects can be complex. Poor documentation can lead to misconfiguration or improper integration, both of which can create security vulnerabilities.
- License Risks – While not a direct security risk, using open source code with incompatible licenses can lead to legal issues, which can indirectly affect the security posture of a project if it leads to hurried code replacements or forks.
Secure Open Source Coding Practices
Despite the aforementioned risks, it is not necessary to forgo the use of open source in the enterprise code base. Then how to secure open source code? , AppSec, DevOps and engineers can ensure secure use of OSS by following these best practices:
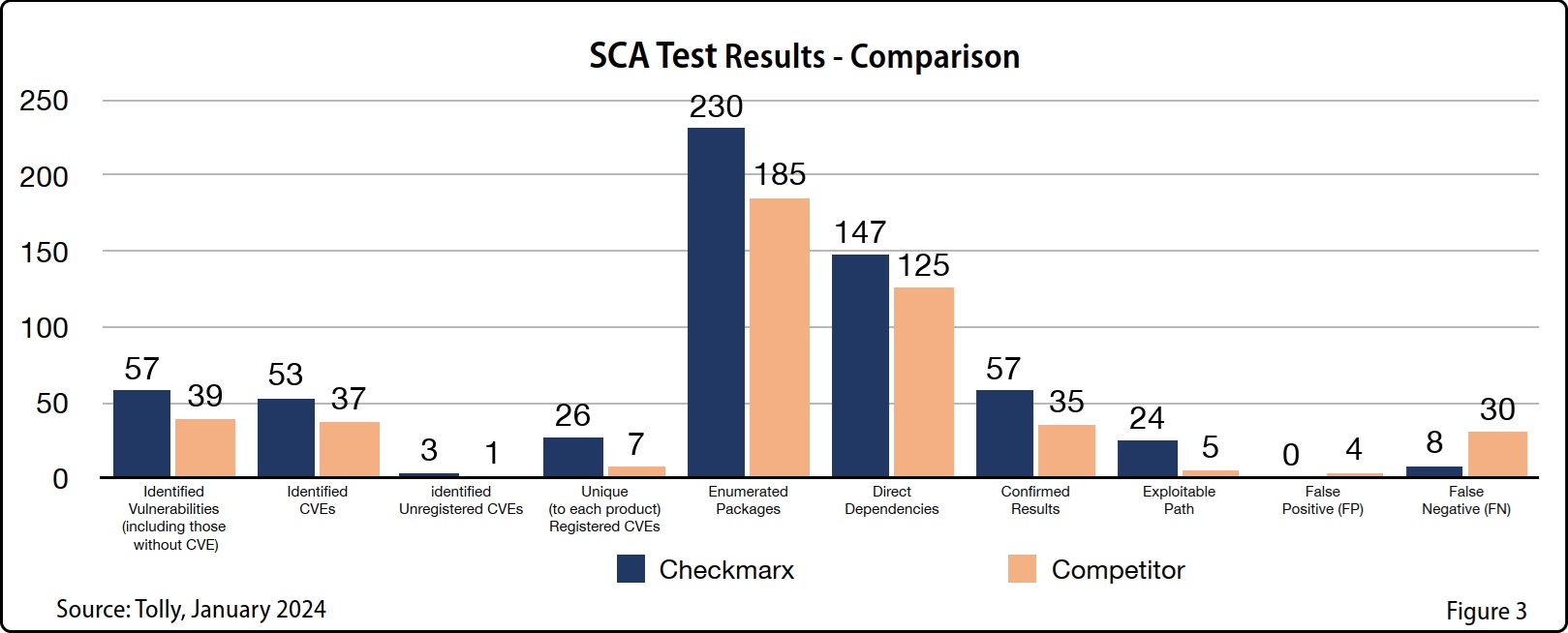
- Regularly Scan for Vulnerabilities – Use automated tools to regularly scan your codebase for known vulnerabilities. Tools like OWASP Dependency-Check and Checkmarx* are effective for detecting vulnerabilities in open source dependencies. *Checkmarx also detects malicious packages, prioritizes risks, provides remediation guidance and generates SBOMs (more details below).
- Prioritize Identified Vulnerabilities – Start by remediating exploitable vulnerabilities, and prioritize efforts based on severity and impact on your specific environment. SCA tools can help with prioritizing, patching, updating and finding safer alternatives.
- Eliminate Noise – Make sure your SCA tool provides relevant outcomes without generating many false positives or false negatives. When evaluating tools, compare their accuracy and reliability with competitors. Reducing noise in vulnerability reports ensures that your developers can focus on real threats and eliminates friction with AppSec.
- Integrate SCA into the Developer Workflow – Shift left with early detection by integrating a developer-friendly SCA solution into the IDE and CI/CD pipelines. This will allow early identification without disruption to development cycles.
- Keep Dependencies Updated – Frequently update all open source libraries and frameworks to their latest versions. This practice helps protect your application from known vulnerabilities found in older versions. Automate this process if you can.
- Contribute to Security – If you discover security issues in open source projects you use, contribute fixes back to the project’s repository. This collaborative approach helps improve security for all users of the open source project.
- Research the Open Source Projects in Use – Thoroughly research the open source projects you are using. Understand their development practices, community activity and how they handle security issues. Monitor the news and cyber feeds for publicized vulnerabilities or exploits. Opt for well-maintained projects with active and responsive communities.
- SBOM – Create a Software Bill of Materials (SBOM) for your projects. An SBOM provides a detailed inventory of all open source components used in your codebase, helping you track and manage these dependencies effectively. In case of a vulnerability, exploited or not, the SBOM will help you understand whether the exploitable packages exist in your enterprise codebase. It is also becoming more common for downstream entities to require SBOMs for third-party software.
- Secure the Developer Workflow – Secure your software supply chain beyond OSS. Implement end-to-end security practices within your development workflow. This includes securing your CI/CD pipelines, using secure coding standards and employing code-signing techniques to ensure code integrity. These can assist in preventing any OSS vulnerabilities from becoming exploitable in your codebase.
- Understand and Manage Licenses – Before using open source components, understand their licenses and ensure they align with your project’s needs, policies and compliance requirements. Mismanaged licenses can lead to legal and operational risks.
- Educate and Train Developers – Regularly train developers on secure coding practices, what to look out for when using OSS libraries and the latest cybersecurity threats.
The SCA Checklist
Here’s an actionable list of steps to take to enhance your SCA approach:
Managing OSS
- Establish clear policies for the use of open source, including acceptable licenses, versions and security standards.
- Track the open source licenses of OSS in use in your applications.
- Update all open source libraries and frameworks to their latest versions.
- Establish a research plan and process for selecting and tracking OSS in use.
Securing the Codebase
- Regularly scan your applications for known vulnerabilities with SCA tools.
- Prioritize identified vulnerabilities according to: 1) Exploitability 2) Severity 3) Impact
- Allocate resources to fix prioritized vulnerabilities.
Securing the SDLC
- Perform code reviews and audits to identify potential security issues.
- Create an automated Software Bill of Materials (SBOM) for your projects.
- Ensure the SBOM is accessible and understandable in case of an attack or known exploit.
- Implement end-to-end security practices within your development workflow: CI/CD, scanning, secure coding and more.
Raising Developer Awareness
- Regularly train developers on OSS risks.
- Establish a team and process for contributing to OSS security through the community.
Checkmarx Software Composition Analysis Solution
Checkmarx protects enterprises from OSS risks and vulnerabilities. With Checkmarx, AppSec teams and CISOs can ensure:
- Software is covered end-to-end
- SCA results are accurate and relevant
- They get visibility not only into OSS vulnerabilities, but also into the presence of malicious packages. Checkmarx analyzes 1 million packages monthly, and has, to date, identified over 200,000 malicious packages
- All OSS dependencies are identified, including dependencies referenced by other dependencies, with unlimited traversal depth
- Remediation is prioritized, guided and actionable
- Irrelevant findings are reduced by 70%
- Scans are conducted regularly via both manual and automatic SCA scan triggering, e.g., scans can be initiated on demand from an integrated IDE or automated as part of a CI/CD workflow
- They can automatically create an SBOM that enhances understanding of OSS risks
- Comprehensive insights into dependencies and associated risks by scanning and analysis of private packages in artifact repositories and internal registries
- Protection against threats posed by malicious open source packages and dependencies within popular AI code generation tools, including ChatGPT
Download the Total Economic Impact report to learn how Checkmarx’ consistently outperforms its competitors.
Get More Accurate AppSec With Checkmarx.
Compared to competitors, Checkmarx Delivers:
- 100% true positives compared to 89.7%
- 50% more known vulnerabilities
- 25% less false positives
Learn more about SCA security with Checkmarx by requesting a demo.