Summary
Static application security testing (SAST) identifies risks in source code or non-live binaries, while dynamic application security testing (DAST) scans running applications for security flaws. Because each type of security test works differently, most teams should use them together to maximize their ability to detect all potential risks.
Which type of application security testing method – SAST or DAST – do you need? The short answer is “both.” SAST and DAST play unique roles in application security, and virtually all organizations should leverage each type of testing to maximize its ability to uncover security risks.
For the longer answer, keep reading as we break down everything you need to know about the differences between SAST and DAST.
SAST vs DAST
Let’s begin by defining what each type of security testing means.
What is SAST?
SAST, which is short for Static Application Security Testing, is a security testing method that scans application source code or static binaries to uncover risks. The main purpose of SAST is to detect known vulnerabilities, such as application code or dependencies that are linked to vulnerabilities recorded as part of CVE databases.
SAST is sometimes called a form of “white box” testing because it involves scanning for security issues from an insider’s perspective. With SAST, you evaluate your applications in a form that typically would not be available to threat actors, who do not usually have access to source code or static binaries.
What is DAST?
DAST, or Dynamic Application Security Testing, is the process of testing running applications. Typically, DAST scans work by simulating the same types of malicious activities that attackers might perform if they were attacking an application in production. Then, DAST tools assess how the application responds to the simulated attacks to determine whether it would be vulnerable in the real world.
DAST is considered a type of “black box” testing because DAST tools scan applications from the same vantage point that attackers have, running code, – from the outside looking in.
Key differences between SAST and DAST
The main differences between SAST and DAST boil down to the following:
- Testing methodology: SAST focuses on testing static code, while DAST tests live applications.
- Testing requirements: SAST tests require access to application source code or static binaries, while DAST requires a live application hosted in a test environment.
- Stage in the SDLC: SAST scans typically occur earlier in the Software Development Lifecycle (SDLC) than DAST tests, which are usually the last major type of security test to occur prior to application deployment.
- Types of risks uncovered: In general, SAST excels at detecting known vulnerabilities, whereas DAST is better at catching security issues that have not been publicly reported – such as those that originate from flaws in original code written by an application’s developers, as opposed to third-party code or dependencies they included in the app.
Combining SAST And DAST For Robust Application Security
Because SAST and DAST serve different purposes, it would be a big mistake to treat SAST as a substitute for DAST, or vice versa. Instead, most teams should perform both types of testing.
It typically makes sense to ask developers to run SAST tests early in the SDLC, in order to uncover common vulnerabilities before developers have gone to the effort of compiling code and deploying it into a test environment. However, once the code is up and running in testing, DAST scans should occur to detect risks that eluded SAST testing.
It’s important to note that even when you perform both SAST and DAST, there’s no guarantee that you’ll detect all risks – even with the help of advanced testing techniques, like AI-powered SAST tests. No testing method is perfect, or guarantees complete coverage of every potential vulnerability or exploit technique that could impact your application. But when you integrate both SAST and DAST into the SDLC, you maximize your chances of detecting risks before your application enters production.
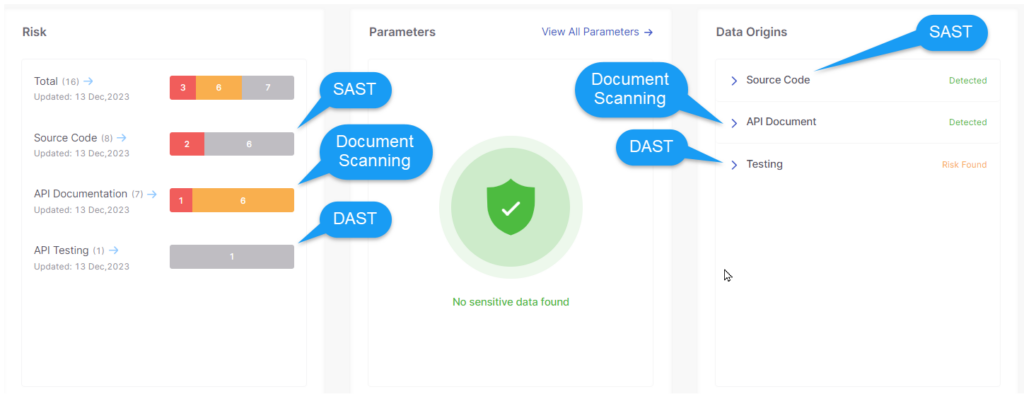
What’s more, by running SAST and DAST on the same AppSec platform, such as Checkmarx One, teams can correlate results from each type of test to gain more context into potential vulnerabilities and risks.
For instance, a SAST scan might reveal that an application includes potentially vulnerable code, but because SAST scans don’t simulate interactions with applications, they can’t definitively confirm that an exploit is possible.
A DAST, however, could achieve this confirmation by testing whether the application actually responds to the exploit technique associated with the potential vulnerability. Based on this insight derived from a combined SAST and DAST testing strategy, engineers would know they should prioritize fixing the issue.
Other types of Application Security Testing
SAST and DAST are not the only types of security testing available. Other common testing and scanning methods include:
- Source Composition Analysis (SCA), which identifies third-party components within applications to catch vulnerabilities and compliance issues.
- Interactive Application Security Testing (IAST). IAST is similar to DAST in that it involves testing live applications, but IAST is usually more hands-on and manual.
- Penetration testing, which also involves testing runtime environments for risks, but which is manual and evaluates the entire environment, not just the application.
A complete application security strategy should leverage all types of relevant testing and correlate results from them to deliver continuous, actionable visibility into security threats.
Optimizing SAST and DAST with Checkmarx One
As a comprehensive application security platform, Checkmarx One delivers the capabilities that teams need to integrate both SAST and DAST tests into the SDLC. No matter which CI/CD tools you use or which types of applications you develop, Checkmarx One continuously and automatically scans for risks using multiple testing methods.
What’s more, by correlating the results of SAST and DAST tests, Checkmarx One provides critical visibility into risks so that your team knows which issues to prioritize and how to remediate them.
To learn more about leveraging Checkmarx One as a comprehensive solution for integrating security across the SDLC, check out our video guide on fine-tuning your AppSec strategy or download our eBook, “7 Best Practices to Increase Developer Adoption of Your AppSec Solution.”